Internet-Is-Dangerous [Defcamp Quals 2023]
Challenge Description
Welcome to the ‘Internet is Dangerous for Kids’ investigation, where you’ll step into the shoes of a cybersecurity investigator tasked with solving a high-stakes kidnapping case. You will learn about a juvenile predator who is luring their victims on social media platforms, ultimately resulting in kidnappings and human trafficking. Its important to know that the cybercriminal managed to establish friendly connections with all of their victims. The cybercriminal’s ultimate goal was to deceive his victims into believing they had won a significant prize of interest, enticing them to visit suspicious places at unusual hours.
Objective Your mission is to follow the digital trail, collect evidence, and uncover the cybercriminals latest kidnapping. To succeed, you’ll need to demonstrate your skills in digital forensics, data analysis, and cyber investigation.
The challenge is divided into 6 questions.
Provided Files
The challenge provides us an archive with c1.ad files which are logical Windows disk images. To open it we need a
software called FTK Imager. We can mount one of the c1.ad files and start our investigation.
Question 1
Provide the OS account name from the live image capture.
Intuition
As it is a Windows logic disk image, we should find the OS account name in the C:\Users.
Solution
Open FTK Imager and go to File > Add Evidence Item. Select image file and then one of the c1.ad files and
click Finish. We can now see the os account name as below:
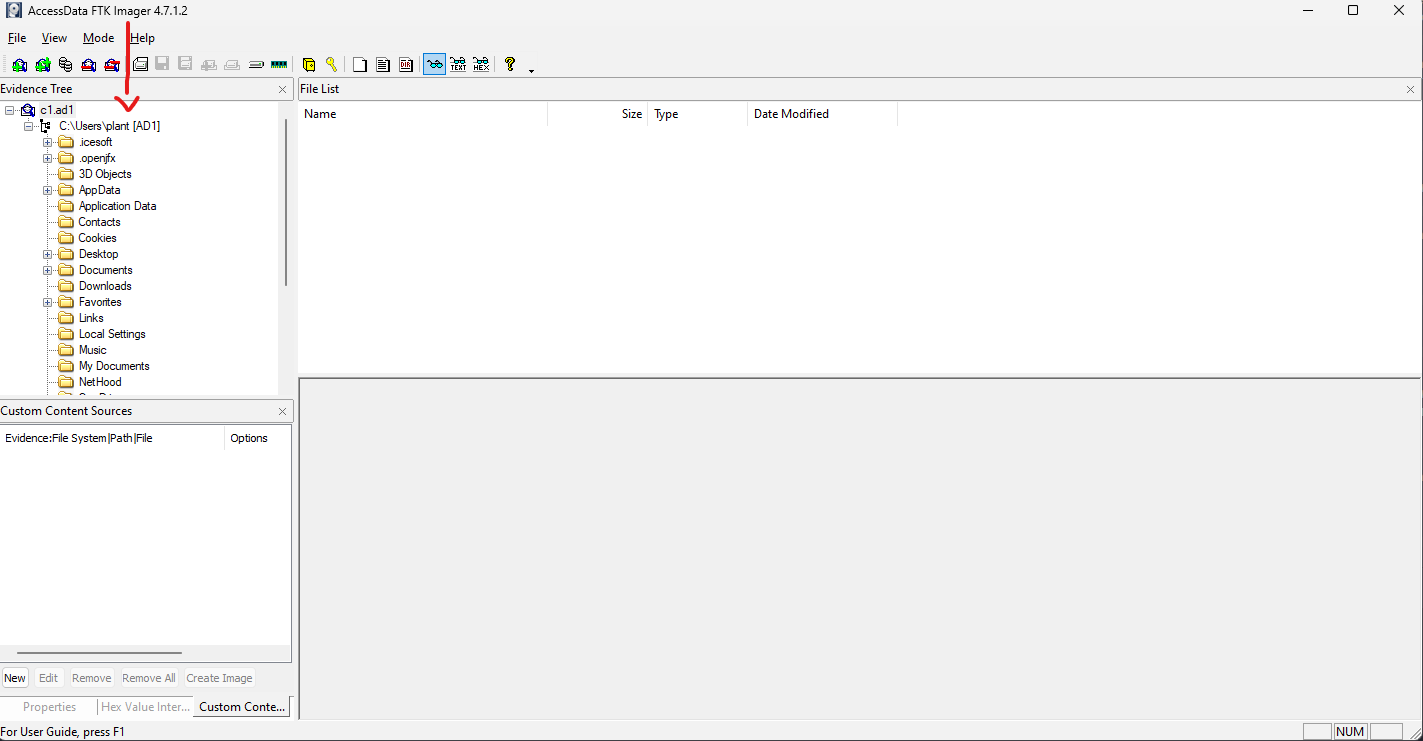
Flag
pant
Question 2
Provide the attacker’s email address.
Intuition
We should find some email logs or files somewhere in the disk image.
Solution
With FTK Imager, go to File > Image mounting. Select one of the c1.ad files and mount it. Next go to the mounted
disk in your file explorer (mine is E:\) and go to the Documents folder. There we can find a file
called connection details - sam jacson jacson (samjacson89@yahoo.com) - 2023-10-09 0317.eml.
Open it using Outlook and there we see the email address of the attacker:
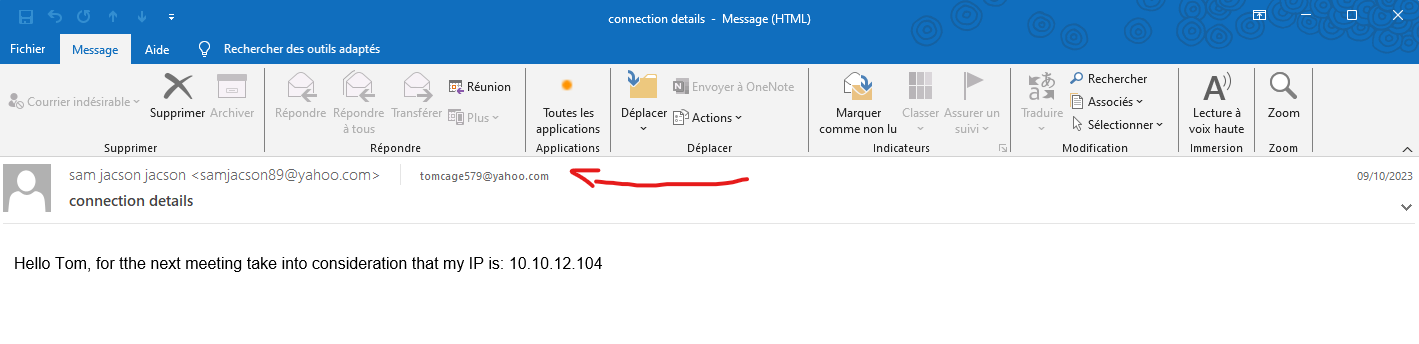
Flag
tomcage579@yahoo.com
Question 3
Provide the victim’s name.
Intuition
First I tried sam-jacson because I used the email address for here but it was not the correct answer.
Solution
If we go to the Desktop folder we can find a file called dont-forget.txt with the following content:
my social media accounts:
facebook:
tomcage579@yahoo.com
TC345204
We can now go to Facebook and login using the credentials tomcage579@yahoo.com:TC345204. I am now connected with the
attacker account and if check his Messnger messages we can see that he is talking with Sam Jackson:
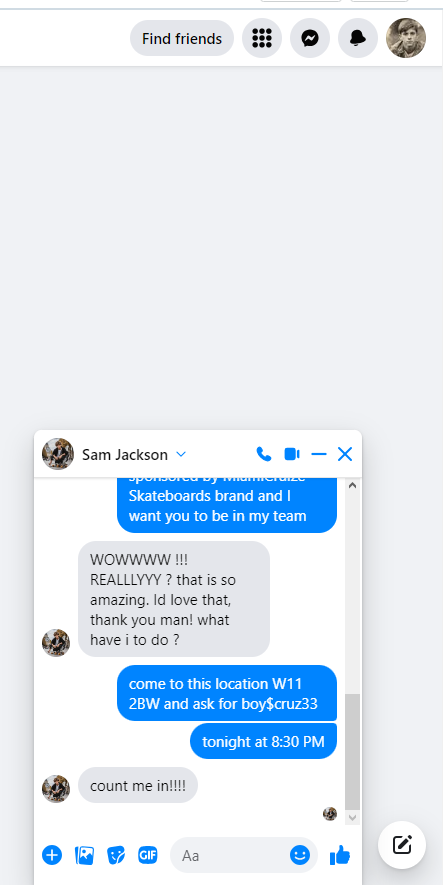 !
!
Flag
sam-jackson
Question 4
Provide the location where the attacker met his victim from the first time face to face.
Intuition
As we can see in the messages of the attacker, he is talking with Sam Jackson and he is asking him to
come to this location W11 2BW. I will search for it on Google Maps.
Solution
If we search for W11 2BW on Google Maps we can see that it is a house in London. The flag is the name of this house.
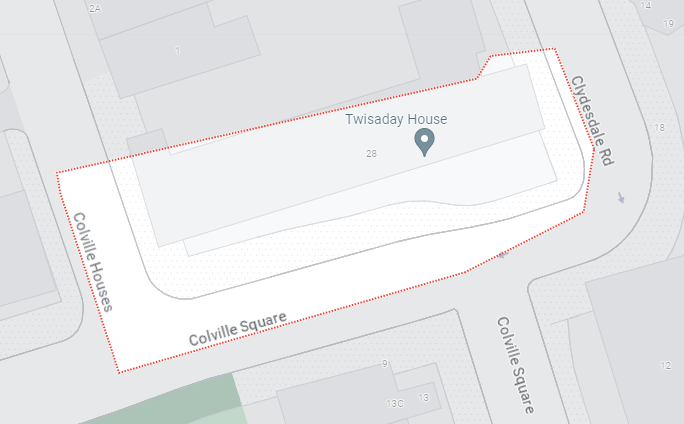
Flag
twisaday-house
Question 5
Provide the address used by the attacker to reach its organisation on dark web.
Intuition
I noticed an image called our_organization.jpg in the Pictures folder and if I use Google lens on it I can see that
it comes from a movie called Unfriend and the movie is related to the Darkweb.
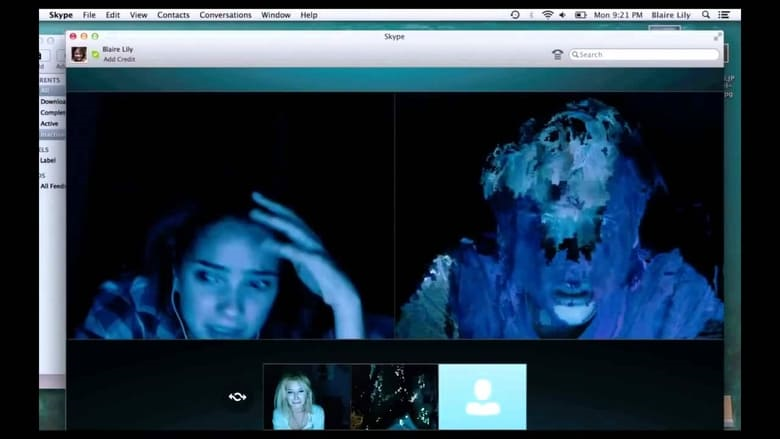
Solution
By opening the image
into Cyberchef
, we quickly notice the hidden onion link in the code of the image.
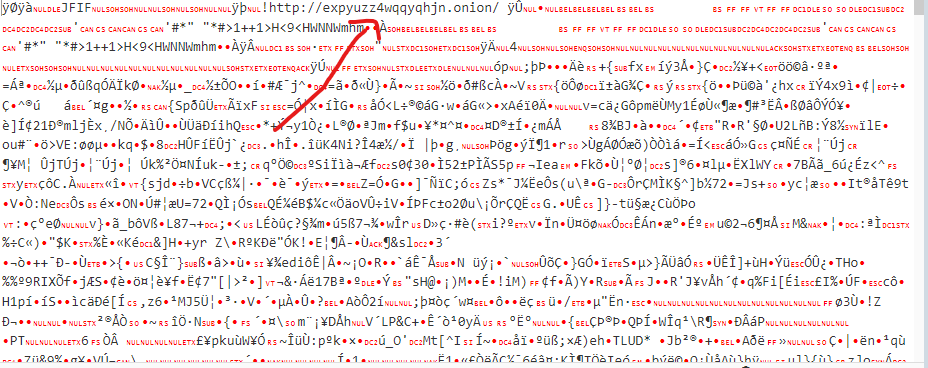
Flag
http://expyuzz4wqqyqhjn.onion
Question 6
Provide the victim’s private IP address.
Intuition
We already found it in the question 2.
Solution
The IP is into the email file we discovered in the question 2.
Flag
10.10.12.104